WireGuard: How to access a peer’s local network
2019-02-25
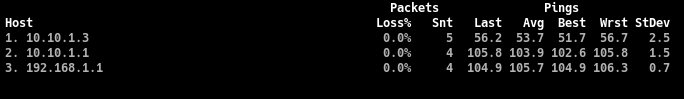
This is a guide about accessing peer A's local network from peer B.
Requirements
- Already setup wireguard network
iptablesinstalled
If you are not familiar with WireGuard's configuration, head to ArchWiki or WireGuard's quickstart guide.
Configs
Server's config
#PeerB
Peer A client config
;
;
Since in my occasion PeerA is a RPi connected wirelessly to the network, notice the wlan0 in PostUp and PostDown commands.
Note
PeerA must have net.ipv4.ip_forward = 1 in kernel parameters.
To do that at runtime pass sudo sysctl net.ipv4.ip_forward=1. For a permanent solution, edit /etc/sysctl.conf with net.ipv4.ip_forward=1.
Peer B client config
Results
This way if peer B pings 192.168.1.1, the traffic is routed through 10.10.1.3 then to 10.10.1.1 and then to 192.168.1.1 as we wanted.
Doing a mtr 192.168.1.1 from peer B: